Posts: 86
Threads: 12
Joined: Aug 2011


So, this game's images have a .png extension but I'm not sure if they have been protected or if they are packed in some form.
Spine files (skel, atlas) and plist are not protected, so maybe images aren't either, either way it's beyond my skillset.
Can someone look into the .png files and see if they are packed in some way or protected?
https://www.mediafire.com/file/n1p0i8stc...0.rar/file
Here's an entire archive, I think it corresponds to a single character.
Posts: 13
Threads: 0
Joined: Nov 2021


(10-08-2021, 07:35 AM)tombmonkey Wrote: So, this game's images have a .png extension but I'm not sure if they have been protected or if they are packed in some form.
Spine files (skel, atlas) and plist are not protected, so maybe images aren't either, either way it's beyond my skillset.
Can someone look into the .png files and see if they are packed in some way or protected?
https://www.mediafire.com/file/n1p0i8stc...0.rar/file
Here's an entire archive, I think it corresponds to a single character.
Any luck? I'm also facing the same issue. I initially tried opening the images by using a program called 'Apk Image Extractor' but it doesn't pick up those encrypted images in the 'Assets' folder. While googling, I may have found a possible solution: [Discussion] A guide to make models of battle cats using SMBX : battlecats (reddit.com)
[Discussion] Finally decrypted BC files with my own scripts!! : battlecats (reddit.com)
That procedure involves using a script to decypt png files. Not sure if it will apply in this instance, but it's worth a shot I suppose. In any case, hopefully somone here more experienced will assist soon.
Posts: 2
Threads: 0
Joined: Dec 2020
Posts: 34
Threads: 7
Joined: Jun 2021
01-24-2022, 12:15 PM
(This post was last modified: 01-24-2022, 12:16 PM by JacintaB2022.)
I'd think the forum site that bihaiorg had just posted could lead us to the answer!
You'll just need the game's APK and a hex editor, and then you'll have to follow the instructions in the site to get the sprites. The site's text is in Chinese though, but just translate the site to English and you'll be fine to go.
Posts: 2
Threads: 0
Joined: Dec 2020
Nice you like this. And I am working on decompiling the .bobj anim file format. It seem to be converted from fla to cocos-2d. Hope to have luck...
Posts: 34
Threads: 7
Joined: Jun 2021
@bihaiorg, I need help on how to extract and convert all of this game's sprites, as i'm not good at hex editing stuff.
By the way, any luck yet on decompiling the .bobj anim file format yet?
Posts: 86
Threads: 12
Joined: Aug 2011


10-17-2022, 02:32 PM
(This post was last modified: 10-17-2022, 03:56 PM by tombmonkey.)
Been so long, didn't see this.
I still have the files from when I originally asked this (1.0.20), there are unencypted spine files there (.skel and .atlas) these can be viewed with http://en.esotericsoftware.com/spine-skeleton-viewer or reimported into the software, but the images are missing obviously.
I checked the latest version I could find (1.7.0) and there are still unencrypted spine files there, if I manage to decode the images then it will be easy to just load the animations on spine.
I have no idea what to do with the info on the chinese website, it looks like they managed to fix the image files but I have no clue how to use that info to actually make something.
Here are some more files if anyone wants to give it a go.
https://www.mediafire.com/file/ou28xw82q...0.zip/file
From looking around it looks like bihaiorg has the image decryption figured out, can't browse that forum without a qq account to check if he ever posted an exe or an useable script.
Here's (I think) his github.
https://github.com/ipengci
Didn't post any tools there either.
Posts: 86
Threads: 12
Joined: Aug 2011


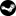
![[Image: hRypqnP.png]](https://i.imgur.com/hRypqnP.png)
Rufaswan managed to crack the code and decrypt the image headers. Now I have to match the images with their corresponding .skel and .json spine files.
Posts: 2
Threads: 1
Joined: Jul 2022
(10-30-2022, 02:04 PM)tombmonkey Wrote: Could you share the tool to decrypt the image headers please? I have had this problem for a long time without any solution.
Posts: 1,489
Threads: 19
Joined: Mar 2020
@AkashiYasuto:
You could write the dev an email and ask nicely for the tool, as stated on his github page:
ipengci (github) Wrote:Repacking
Repacking is not yet implemented, maybe never.
Note:
This is in progressing, sorry for the delay! Please send e-mail to 326812493@139.com to get the tools by now. Source:
https://github.com/ipengci/StreetFighterDuel_Tools
Posts: 161
Threads: 4
Joined: Jul 2017


12-10-2022, 09:42 PM
(This post was last modified: 12-10-2022, 11:11 PM by rufaswan.)
Actually @bihaiorg already posted the solution, the code from 52pojie.cn looks very complex, but it can be simplified to
Code: if ( v10 == *(_QWORD *)"VEGATOPJOY000000VEGATOPJOY000000N7cocos2d5ImageE" )
{
v33 = v10;
v34 = v9;
v35 = v11;
v3 -= 16;
v12 = v4[23];
v4 += 16;
*v4 ^= 0x51u;
v4[1] = v4[1] ^ 0x49;
v4[2] = v4[2] ^ 0x51;
v4[3] = v4[3] ^ 0x49;
v4[4] = v4[4] ^ 0x41;
v4[5] = v4[5] ^ 0x4E;
v4[6] = v4[6] ^ 0x52;
v4[7] = v12 ^ 0x41;
v4[8] = v4[8] ^ 0x4E;
v4[9] = v4[9] ^ 0x58;
v4[10] = v4[10] ^ 0x49;
v4[11] = v4[11] ^ 0x41;
v4[12] = v4[12] ^ 0x4F;
v4[13] = v4[13] ^ 0x42;
v4[14] = v4[14] ^ 0x45;
v4[15] ^= 0x49u;
}
What the code basically means - check the first 16 bytes for "VEGATOPJOY000000", then XOR the next 16 bytes with "51 49 51 49 41 4e 52 41 4e 58 49 41 4f 42 45 49". That is the ASTC image header. The rest are ASTC image data, and they are unencrypted..
Re-save the ASTC image part as *.ASTC file, and you can use this tool to convert them
https://github.com/ARM-software/astc-encoder/releases
Run in command line like this
Code: astcenc-sse2.exe -dl IN.ASTC OUT.PNG
The tool can also encode the edited PNG back. Just XOR the ASTC header, and then prepend "VEGATOPJOY000000" back to the file. It's very easy.
Thanks for @bihaiorg for figured the whole thing out and sharing the code!
- Rufas
Posts: 13
Threads: 0
Joined: Nov 2021


12-20-2022, 08:52 PM
(This post was last modified: 12-20-2022, 08:53 PM by Hollow.)
(12-10-2022, 09:42 PM)rufaswan Wrote: Actually @bihaiorg already posted the solution, the code from 52pojie.cn looks very complex, but it can be simplified to
Code: if ( v10 == *(_QWORD *)"VEGATOPJOY000000VEGATOPJOY000000N7cocos2d5ImageE" )
{
v33 = v10;
v34 = v9;
v35 = v11;
v3 -= 16;
v12 = v4[23];
v4 += 16;
*v4 ^= 0x51u;
v4[1] = v4[1] ^ 0x49;
v4[2] = v4[2] ^ 0x51;
v4[3] = v4[3] ^ 0x49;
v4[4] = v4[4] ^ 0x41;
v4[5] = v4[5] ^ 0x4E;
v4[6] = v4[6] ^ 0x52;
v4[7] = v12 ^ 0x41;
v4[8] = v4[8] ^ 0x4E;
v4[9] = v4[9] ^ 0x58;
v4[10] = v4[10] ^ 0x49;
v4[11] = v4[11] ^ 0x41;
v4[12] = v4[12] ^ 0x4F;
v4[13] = v4[13] ^ 0x42;
v4[14] = v4[14] ^ 0x45;
v4[15] ^= 0x49u;
}
What the code basically means - check the first 16 bytes for "VEGATOPJOY000000", then XOR the next 16 bytes with "51 49 51 49 41 4e 52 41 4e 58 49 41 4f 42 45 49". That is the ASTC image header. The rest are ASTC image data, and they are unencrypted..
Re-save the ASTC image part as *.ASTC file, and you can use this tool to convert them
https://github.com/ARM-software/astc-encoder/releases
Run in command line like this
Code: astcenc-sse2.exe -dl IN.ASTC OUT.PNG
The tool can also encode the edited PNG back. Just XOR the ASTC header, and then prepend "VEGATOPJOY000000" back to the file. It's very easy.
Thanks for @bihaiorg for figured the whole thing out and sharing the code!
- Rufas
"Re-save the ASTC image part as *.ASTC file"
Pardon me, how exactly do I accomplish this? Is there an option for this in the hex editor?
Posts: 161
Threads: 4
Joined: Jul 2017


(12-20-2022, 08:52 PM)Hollow Wrote: "Re-save the ASTC image part as *.ASTC file"
Pardon me, how exactly do I accomplish this? Is there an option for this in the hex editor?
If you are using a hex editor and doing it manually,
1. use the DELETE key to remove "VEGATOPJOY000000" (the first 16 bytes of the file).
2. Now, the first 16 bytes of the file is the ASTC image header, you'll need to XOR with the key above.
3. Re-save the file by File -> Save as and change the file extension from .png to .astc.
To encode back, reverse the 3 steps above.
- Rufas
Posts: 13
Threads: 0
Joined: Nov 2021


(12-24-2022, 08:21 PM)rufaswan Wrote: (12-20-2022, 08:52 PM)Hollow Wrote: "Re-save the ASTC image part as *.ASTC file"
Pardon me, how exactly do I accomplish this? Is there an option for this in the hex editor?
If you are using a hex editor and doing it manually,
1. use the DELETE key to remove "VEGATOPJOY000000" (the first 16 bytes of the file).
2. Now, the first 16 bytes of the file is the ASTC image header, you'll need to XOR with the key above.
3. Re-save the file by File -> Save as and change the file extension from .png to .astc.
To encode back, reverse the 3 steps above.
- Rufas
Ok thanks. What program or hex editor are you using to accomplish this? I'm using Hex Editor Neo and there are no options that I'm aware of that allow me to save the file extension as .astc.
Posts: 13
Threads: 0
Joined: Nov 2021


(12-24-2022, 08:21 PM)rufaswan Wrote: (12-20-2022, 08:52 PM)Hollow Wrote: "Re-save the ASTC image part as *.ASTC file"
Pardon me, how exactly do I accomplish this? Is there an option for this in the hex editor?
If you are using a hex editor and doing it manually,
1. use the DELETE key to remove "VEGATOPJOY000000" (the first 16 bytes of the file).
2. Now, the first 16 bytes of the file is the ASTC image header, you'll need to XOR with the key above.
3. Re-save the file by File -> Save as and change the file extension from .png to .astc.
To encode back, reverse the 3 steps above.
- Rufas
Hello? Are you there? Could you direct me to or recommend a hex editor that allows me to both XOR and re-save the file as an .astc file? I can't go any further at the moment.
|





![[Image: yXqxjiu.png]](http://i.imgur.com/yXqxjiu.png)
![[Image: 133748wrvl2ywyvhknv9av.gif]](https://attach.52pojie.cn/forum/202201/14/133748wrvl2ywyvhknv9av.gif)
![[Image: hRypqnP.png]](https://i.imgur.com/hRypqnP.png)